Based on our research, here are the top 5 cyber threats hanging over your head
“There are only two types of companies: those that have been hacked, and those that will be,” said Robert Mueller. This isn’t coming from any Tom, Dick, or Harry; it’s coming from a guy who spent twelve of his years serving as the director of one of the biggest federal security agencies in the world – the FBI.
As you’ve landed on this page, we believe that you belong to the latter type of companies, and of course, you’d like it to stay that way. So, let us help you with that. Based on our research and years of experience, we’ve enlisted here the five most common types of cyber-attacks your company is likely to face these days.
So, here are the top 5 Types of Cyber Attacks Your Company is Highly Likely to Face. Watch out!
1. Ransomware Attacks & Financial Malware Attacks
2017 was the year that most people finally added this unfamiliar word to their own dictionary, and that word is ‘ransomware.’ It’s pretty much what it sounds like – you must pay a ransom to get something back, and that something, in this case, is your own data. To make matters even worse, you must pay within a specified time, and the payment must be in cryptocurrencies (mostly Bitcoin).
These ransomware attacks lock out your own system and leave a message like this on your screen asking for the ransom.
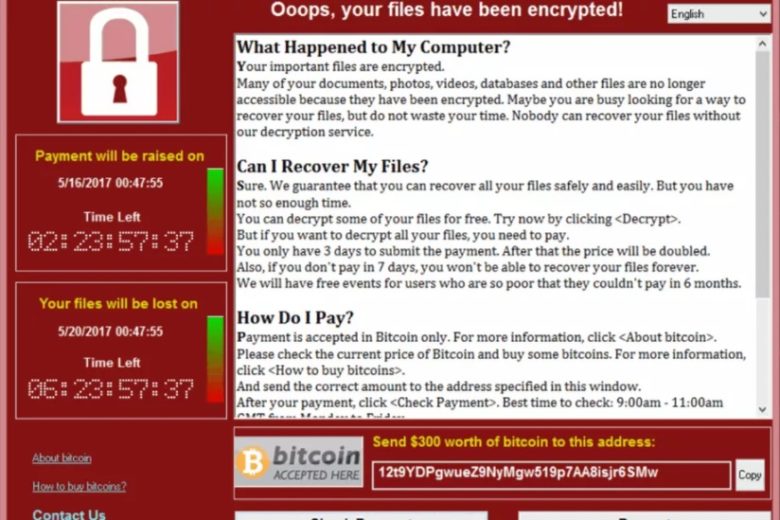
Looks like the script of a classic Liam Neeson movie, doesn’t it?
And you know what? These attacks have gone to the next level in the form of Ransomware-as-a-service (RaaS) attacks. It means that one can hire an attacker to attack someone’s system. This presents a golden opportunity to the wannabe hackers who have zero (or negative) skills.
Another type of attack that often goes under the radar is Financial Malware. Chances are, you may never have heard of it. Click here to learn more about them.
It’s a scary world out there, isn’t it?
2. Phishing Scams
What do you do when you want to trick someone into giving their confidential information? You employ a phishing attack that’s what. E-mails are found to be a hacker’s favorite weapons to fool people into giving their information.
The attackers circulate e-mails that are tempting to click on. Once you click on that e-mail, you’re redirected to a website that has malicious files and your system will get infected by those files. Phishing rightly said!
3. Data Breach
When it comes to data breaches, bigger organizations are the primary targets of hackers. After all, where else do you get private information of millions of users? Where else do you get to be on the first page of Google? That’s why we saw a host of big companies becoming the victims of data breaches. Equifax, Yahoo, Uber, Alteryx, Dun & Bradstreet; these are some of the most high-profile victims that suffered the wrath of data breaches in 2017.
However, it doesn’t mean that smaller companies don’t need to worry about data breaches. In fact, they should be worried even more. According to a study, 90% of the breaches impact small businesses. This is because of the inadequacy of proper security practices in such organizations. The smaller businesses should take every measure to prevent such breaches as they pose a danger on their very existence.
4. Man in the Middle (MITM) Attack
Remember Harry Caul from the movie The Conversation (1974)? Me neither, but he was one hell of a bugger. So good that he was named “the best bugger on the west coast.” From 1974 to 2017, everything has changed and so have the techniques of “bugging.” A MITM attack is the latest form of wiretapping, without the use of wires (spooky).
As you can see on our website, there’s a secure sign at the front of our URL with our company name inscribed on it. That means that your system is currently talking to our servers and there is no one in between as we’ve installed an SSL/TLS certificate on our website. If a perpetrator wants to execute a MITM attack in between us, he/she’d establish a connection with your system and make you believe that you’re talking to us, but that won’t be the case. Therefore, any information you send to our website will come through the attacker, and he/she will be able to see all the information that you send.
5. Denial-of-Service (DoS) Attack
Denial-of-Service is the new ‘buried under the paperwork.’ In legal dramas, we’ve seen episodes where one party sends an awful lot of paperwork in order to slow the other party down. In today’s age, one sends an awful lot of traffic to a competitor’s website to the extent that the website cannot handle such traffic and ultimately gets crashed. There are other types of DoS attacks such as Reflective attacks and Resource exhaustion, but volumetric-floods (Traffic based) are employed on a wider basis.
Needless to say, this could hurt you regarding your reputation as well as your earnings.
If you don’t want to put up ‘Sorry, we’re closed’ poster on your website, we recommend setting up a Next-Generation Firewall as the first line of defense.
In today’s era of cut-throat competition, anything is possible!
Final Word
Dealing with Cyber Security is a lot like riding a bicycle. You must watch what’s ahead of you, what’s beside you, what’s behind you and keep on peddling at the same time so that your bicycle doesn’t stop and you don’t fall over.







